
The Battle of Britain data base came into existence at the request of OSD PA&E (Office of the Secretary of Defense, Program Analysis and Evaluation). They contacted us. They were working with LMI (Logistics Management Institute, on of a dozen FFRDCs) to develop an air combat model. They felt that the Battle of Britain would be perfect for helping to develop, test and validate their model. The effort was led by a retired Air Force colonel who had the misfortune of spending part of his career in North Vietnam.
The problem with developing any air campaign database is that, unlike the German army, the Luftwaffe actually followed their orders late in the war to destroy their records. I understand from conversations with Trevor Dupuy that Luftwaffe records were stored in a train and had been moved to the German countryside (to get them away from the bombing and/or advancing armies). They then burned all the records there at the rail siding.
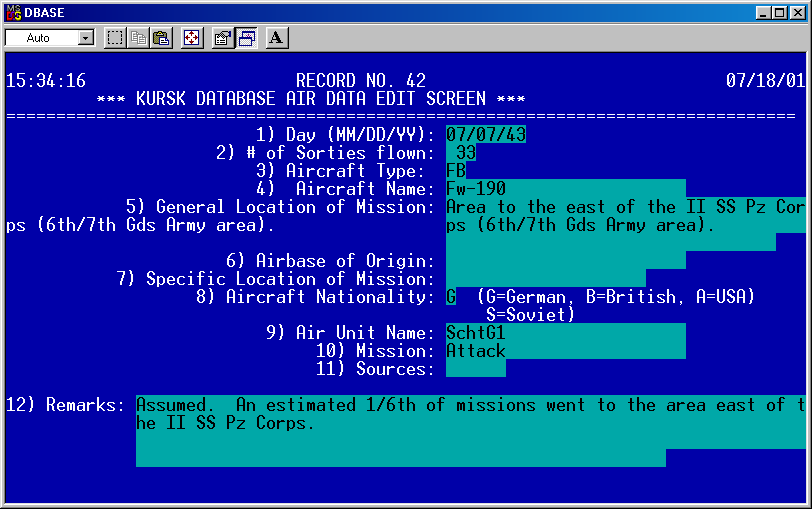
So, when HERO (Trevor Dupuy’s Historical Evaluation Research Organization) did their work on the Italian Campaign (which was funded by the Air Force), they had to find records on the German air activity with the Luftwaffe liaison officers of the German armies involved. The same with Kursk, where one of the few air records we had was with the air liaison officer to the German Second Army. This was the army on the tip of the bulge that was simply holding in place during the battle. It was the only source that gave us a daily count of sorties, German losses, etc. Of the eight or so full wings that were involved in the battle from the VIII Air Corps, we had records for one group of He-111s (there were usually three groups to a wing). We did have good records from the Soviet archives. But it hard to assemble a good picture of the German side of the battle with records from only 1/24th of the units involved. So the very limited surviving files of the Luftwaffe air liaison officers was all we had to work with for Italy and Kursk. We did not even have that for the Ardennes. Luckily the German air force simplified things by flying almost no missions until the disastrous Operation Bodenplatte on 1 January 1945. Of course, we had great records from the U.S. and the UK, but….hard to develop a good database without records from both sides. Therefore, one is left with few well-documented air battles anywhere for use in developing, evaluating and validating an air campaign model.
The exception is the Battle of Britain, which has been so well researched, and extensively written about, that it is possible to assemble an accurate and detailed daily account for both sides for every day of the battle. There are also a few surviving records that can be tapped, including the personal kill records of the pilots, the aircraft loss reports of the quartermaster, and the ULTRA reports of intercepted German radio messages. Therefore, we (mostly Richard Anderson) assembled the Battle of Britain data base from British unit records and the surviving records and the extensive secondary sources for the German side. We have already done considerable preliminary research covering 15 August to 19 September 1940 as a result of our work on DACM (Dupuy Air Combat Model)
The database covered the period from 8 August to 30 September 1940. It was programmed in Access by Jay Karamales. From April to July 2004 we did a feasibility study for LMI. We were awarded a contract from OSD PA&E on 1 September to start work on the database. We sent a two-person research team to the British National Archives in Kew Gardens, London. There we examined 249 document files and copied 4,443 pages. The completed database and supporting documentation was delivered to OSD PA&E in August 2005. It was certainly the easiest of our campaign databases to do.
We do not know if OSD PA&E or LMI ever used the data base, but we think not. The database was ordered while they were still working on the model. After we delivered the database to them, we do not know what happened. We suspect the model was never completed and the effort was halted. The database has never been publically available. PA&E became defunct in 2009 and was replaced by CAPE (Cost Assessment and Program Evaluation). We may be the only people who still have (or can find) a copy of this database.
I will provide a more detailed description of this database in a later post.


 This blog
This blog 

